Guidance for Building an Enterprise-Ready Network Foundation for RISE with SAP on AWS
Summary: This implementation guide provides an overview of the Guidance for Enterprise-Ready Network Foundation for RISE with SAP on AWS, its reference architecture and components, considerations for planning the deployment, and configuration steps for deploying the Guidance name to Amazon Web Services (AWS). This guide is intended for solution architects, business decision makers, DevOps engineers, data scientists, and cloud professionals who want to implement a Landing Zone for RISE with SAP in their AWS environment.
Implementation Guide for Building an Enterprise-Ready Network Foundation for RISE with SAP on AWS
Guidance Overview
This implementation guide provides detailed steps for building a secure and scalable multi-account landing zone for RISE with SAP relevant and customer-managed workloads on AWS. The landing zone is created using the Landing Zone Accelerator on AWS, an AWS Solution that automates the setup of a multi-account AWS environment aligned with AWS best practices.
The implementation guide focuses on establishing resilient network connectivity between a customer’s on-premises environment and the RISE with SAP deployment running on AWS. This includes setting up AWS Direct Connect as the primary connection with AWS Site-to-Site VPN as a failover option. The guide also covers integrating the network connectivity into the overall landing zone architecture managed by the Landing Zone Accelerator.
Additionally, the Guidance outlines steps for configuring security and monitoring controls using services such as AWS Network Firewall. This helps ensure the landing zone environment is secured and provides fine-grained control over network traffic.
Beyond establishing essential services for networking and security, the guide provides a foundation for setting up complementary workloads that are not hosted by RISE with SAP (for example, specific bank encryption system, SFTP servers, and others).
Intended audience:
This implementation guide is intended for AWS customers who are using RISE with SAP and need to set up a secure, scalable, and well-architected AWS landing zone to support and extend their RISE with SAP environment as well as any additional customer-managed workloads that may be adjacent to or integrated with RISE with SAP.
This Guidance is applicable for:
- Customers who are migrating their SAP landscape to RISE with SAP on AWS and need to establish the necessary network connectivity and security controls within an AWS landing zone.
- Customers who have existing on-premises infrastructure and applications that need to integrate with their RISE with SAP environment running on AWS.
- AWS Partners and systems integrators who are helping customers implement RISE with SAP on AWS and need to set up the supporting AWS landing zone and network architecture.
The Guidance provides a comprehensive approach to building out the AWS landing zone to support the RISE with SAP use case, as well as the flexibility to accommodate other customer-managed workloads running alongside RISE with SAP. It covers the essential networking, security, and operational aspects to ensure a resilient and well-governed AWS environment.
Key Concepts
- Landing Zone: A well-architected, multi-account AWS environment that is scalable and secure. This is a starting point from which your organization can quickly launch and deploy workloads and applications with confidence in your security and infrastructure environment.
- Landing Zone Accelerator on AWS: The Landing Zone Accelerator is an AWS Solution that automates the deployment and configuration of a secure, well-architected landing zone on AWS. It sets up core AWS services and best practices to provide a strong foundation for your workloads.
- AWS CDK: CDK is an open-source software development framework used to define cloud infrastructure in code. The Landing Zone Accelerator leverages CDK to provision the landing zone resources.
- AWS CloudFormation: CloudFormation is an AWS service that allows you to define your infrastructure as code. The Landing Zone Accelerator uses CloudFormation templates to deploy the landing zone.
- Configuration Files: The Landing Zone Accelerator uses various configuration files, such as for networking settings, to customize the landing zone deployment for your specific requirements.
- GitHub: The Landing Zone Accelerator is available as an open-source project on GitHub, allowing you to access the code and documentation and collaborate on improvements.
- Organizational Units (OUs): The Landing Zone Accelerator sets up a hierarchical structure of OUs to organize your AWS accounts and apply consistent policies and configurations.
- AWS Direct Connect: The Landing Zone Accelerator integrates with Direct Connect to enable a dedicated, private network connection between your on-premises infrastructure and the AWS environment.
- AWS Site-to-Site VPN: The Landing Zone Accelerator also supports the configuration of a Site-to-Site VPN connection as a backup or alternative to the Direct Connect link.
- AWS Transit Gateway: The Landing Zone Accelerator configures a Transit Gateway to simplify network routing and enable secure communication between your VPCs and on-premises networks.
- SAP Connectivity Questionnaire: This is a spreadsheet document provided by SAP that helps gather the necessary information to connect your RISE with SAP environment to your AWS landing zone.
- AWS Network Firewall: This is a managed service that makes it easy to deploy essential network protections for all of your Amazon Virtual Private Clouds (VPCs).
Architecture Overview
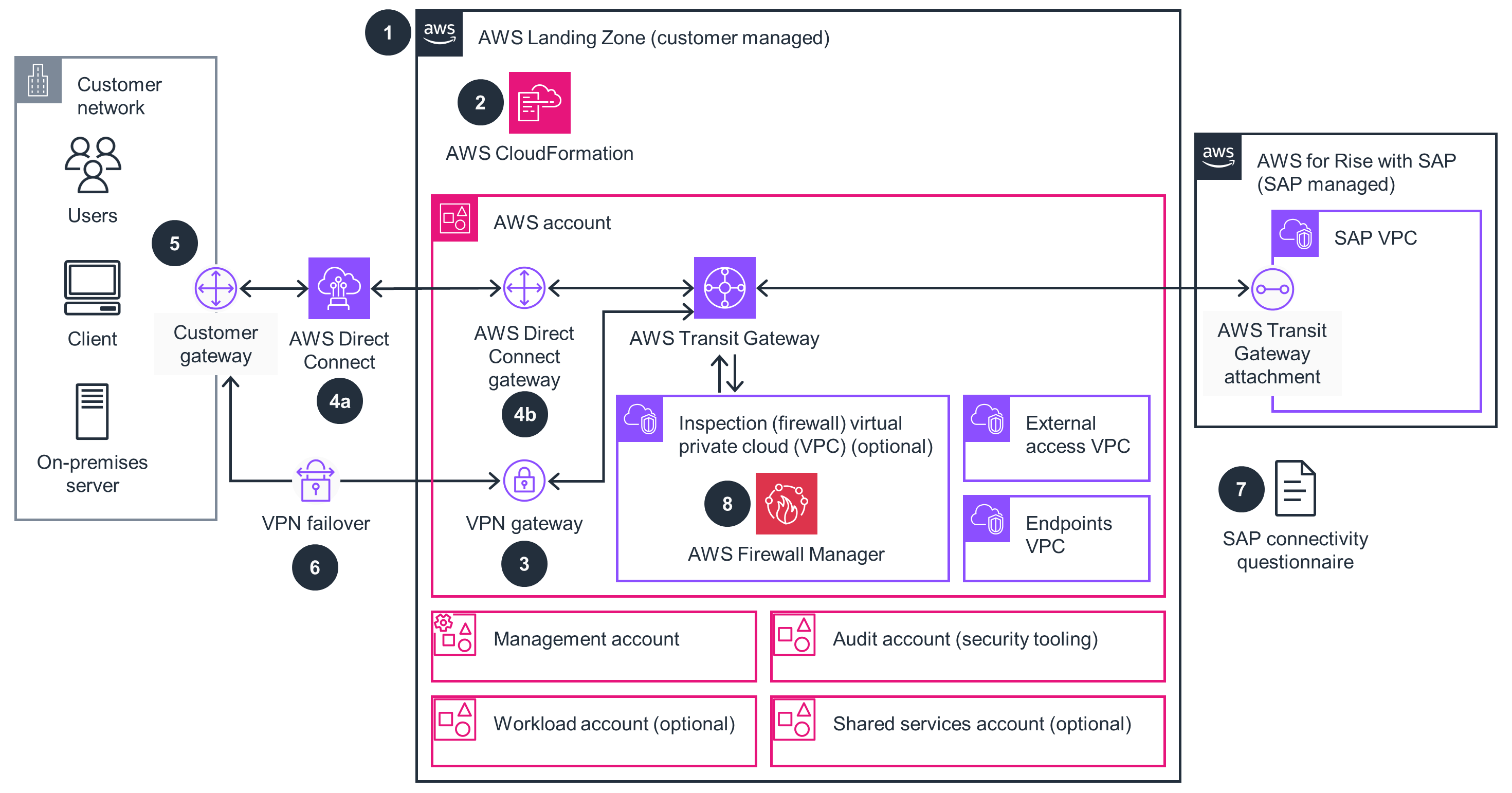
Figure 1: Architecture Steps Diagram
Architecture Steps
- Create an AWS account. Follow this guide if you do not already have one. This establishes your fundamental AWS presence and access to AWS services.
- Deploy the installer stack for Landing Zone Accelerator environment using either the documentation for a deployment based on AWS CDK or the documentation for a deployment based on CloudFormation. This sets up the foundational multi-account AWS environment structure using the Landing Zone Accelerator.
- (Optional) Configure the Site-to-Site VPN Gateway within the Landing Zone Accelerator on AWS networking config file. This enables a secure, encrypted tunnel between the on-premises network and AWS.
- (Optional) Request an AWS Direct Connect connection through the AWS Management Console, then order the Direct Connect connection(s) with an AWS Partner or network provider. This establishes dedicated private network connection between the on-premises network and AWS.
Depending on the type of connectivity and on-premises locations, establishing connectivity may take hours, or it may take weeks or months. Review the AWS Direct Connect Getting Started page for more details. a. Update Direct Connect gateway’s virtual interface with your Direct Connect physical connection ID (obtained above) within the Landing Zone Accelerator on AWS networking config file. This links your physical Direct Connect connection to your AWS environment configuration.
- Configure your network’s customer gateway device for the Site-to-Site VPN and the Direct Connect connection to enable your on-premises network equipment to communicate with AWS.
- Configure Direct Connect and Site-to-Site VPN for failover. This enables continuous connectivity by enabling automatic switching between Direct Connect and the VPN.
- Provide your AWS Transit Gateway details to SAP (using the AWS connectivity questionnaire provided by SAP) to connect to the RISE with SAP environment, then accept the incoming transit gateway association request. This enables network connectivity between your AWS environment and RISE with SAP.
- (Optional) Configure the AWS Network Firewall within Landing Zone Accelerator on AWS to secure the connectivity between your network and the RISE with SAP environment.
Plan your Deployment
Network Considerations
Establishing reliable and secure network connectivity between the customer’s network environment and the RISE with SAP deployment on AWS is a critical aspect of this Guidance. Several key networking factors must be considered to ensure the Guidance meets the performance, availability, and security requirements.
First, customers must ensure their corporate network infrastructure is ready to integrate with their chosen AWS networking services. This includes configuring Border Gateway Protocol (BGP) on their routers with MD5 authentication, a requirement for using Direct Connect. Customers should also verify that their network can support multiple BGP connections for redundancy, as recommended for a highly available setup. Site-to-Site VPN also requires BGP Autonomous System Number (ASN) depending on the type of routing chosen.
You must review and select a resiliency option to ensure you use the right approach for your resiliency needs. The option you choose affects your connection uptime Service Level Agreement (SLA). This Guidance only covers one of several possible configurations, namely one Direct Connect configuration and one failover Site-to-Site VPN configuration. Review AWS SAP Guides on RISE with SAP Connectivity and AWS Direct Connect Resiliency Recommendations for more information.
The Guidance recommends that customers review the AWS documentation on both Direct Connect and Site-to-Site VPN. BGP with AWS Direct Connect provides detailed information on the necessary router configurations and best practices. To learn more about the requirements from your network, review Network Requirements under the AWS Direct Connect User Guide. View the prerequisites for Site-to-Site VPN in the User Guide.
Additionally, review Getting started with Direct Connect. You can optionally review the Hybrid Connectivity AWS Whitepaper for a deeper understanding.
Within the AWS environment, the Landing Zone Accelerator will provision the necessary networking resources, such as Virtual Private Clouds (VPCs), subnets, and network gateways. Customers should ensure that the networking OU within their Landing Zone Accelerator deployment is properly set up to host the configurations for the Direct Connect and VPN connections.
When ordering the Direct Connect connection, customers have the option to choose between a Dedicated Direct Connect or a Hosted Direct Connect, depending on their specific requirements and infrastructure. This guide provides instructions for both connection types, including the necessary steps for ordering the connection and integrating it into the Landing Zone Accelerator configuration. Point-of-presence (POP) is another option for Direct Connect. POP is a physical cross-connect that allows users to establish a network connection from their premises to an AWS Region or AWS Local Zone. You can use the nearest Direct Connect POP to benefit from lower setup and running cost, with the same or lower network latency to your RISE with SAP VPC that runs on the parent AWS Region. For more information, review our AWS documentation for RISE with SAP.
For the AWS Site-to-Site VPN, customers must ensure their firewalls allow the necessary traffic for the VPN tunnels. Customers should also confirm they have two customer gateway devices or a single device capable of managing multiple VPN tunnels, as required for the active/passive VPN configuration.
Deploy the Guidance
Prerequisites
- Ensure you have an active AWS account. If you don’t have one, you can create a new AWS account following these instructions.
- Read the blog post on Building Resilient Network Connectivity for RISE with SAP on AWS.
- Complete the prerequisites for the Landing Zone Accelerator on AWS.
- Familiarize yourself with the concept of landing zones and why they are recommended for AWS environments.
- Review the implementation guide for the Landing Zone Accelerator.
- Understand the standard configuration provided as a base for the Landing Zone Accelerator.
- Go through the Landing Zone Accelerator workshop to get hands-on experience.
Implementation Steps
1. Deploy Installer Stack for Landing Zone Accelerator
For comprehensive step-by-step instructions on deploying the Landing Zone Accelerator Installer stack, refer to the installation guide.
The key steps are creating a GitHub token, storing it securely, and then deploying the Installer stack using the generated CloudFormation template.
Self-hosting with Amazon S3 is required.
2. Update the Landing Zone Accelerator with standard configuration
The configuration of the Landing Zone Accelerator is managed through configuration files. Configuration files are written in YAML and define the AWS account and service configurations that meet specific compliance objectives. Using the configuration files, the Landing Zone Accelerator helps users manage the lifecycle of their landing zone by setting up a baseline security architecture and automating common administrative and operational activities. This reduces the undifferentiated heavy lifting associated with building regulated environments on AWS, allowing organizations to focus on other high value concerns such as operating models, developer agility, and reducing costs.
2.1 Wait for installer stack to finish creating
2.2 Update configuration files with standard sample configuration Follow the steps outlined in the Landing Zone Accelerator user implementation guide to use Amazon Simple Storage Service (Amazon S3) to update the configuration files with the sample configuration files.
Understand more about what the standard configuration for the Landing Zone Accelerator is by reading the overview.
3. (Optional) Create Site-to-Site VPN with Landing Zone Accelerator
This approach to setting up the Site-to-Site VPN can be implemented before or in parallel with the Direct Connect configuration. Configuring the VPN may be a faster way to establish initial network connectivity between your on-premises environment and the RISE with SAP deployment on AWS, compared to provisioning the DX connection, which can sometimes take weeks or months.
Even though the VPN is set up separately from the DX connection, it can still be managed and maintained within the overall Landing Zone Accelerator infrastructure. This provides a unified and automated way to manage your network connectivity, whether it’s the primary Direct Connect link or the VPN failover.
Some key use cases for implementing the Site-to-Site VPN alongside the Direct Connect connection include:
- Providing temporary network access for agile teams or project-based workloads
- Enabling global connectivity
- Achieving high availability and failover
While Direct Connect provisions your hosted/dedicated connections, you can begin preparing your corporate network infrastructure for the VPN setup. Follow the prerequisites for more details.
The AWS Site-to-Site VPN connection consists of three key components:
- Virtual Private Gateway (VGW) - The router on the AWS side here
- Customer Gateway (CGW) - The router on the customer side. See example code: here
- The Site-to-Site VPN connection that binds the VGW and CGW together over two secure IPSec tunnels in an active/passive configuration here
The customer gateway resource in AWS does not configure or create the customer gateway device. You must configure the device yourself.
For in-depth documentation on establishing the AWS Site-to-Site VPN connection, refer to the AWS documentation here.
3.1 Update Landing Zone Accelerator networking configuration file with VPN In the Landing Zone Accelerator networking configuration YAML file, locate the section for VPN connections and add the necessary details.
3.2 Save the updated YAML file and commit the changes to your Landing Zone Accelerator configuration repository.
3.3 Deploy the updated Landing Zone Accelerator configuration to create the Site-to-Site VPN connection.
4. (Optional) Order Direct Connect connection.
Depending on the type of connectivity and on-premises locations, connectivity can be established within hours, however, it may take weeks or months. Consider first implementing Site-to-Site VPN to establish connection between your corporate network and your RISE with SAP on AWS environment.
4.1 Create new Direct Connect connection Use the Direct Connect tab on the AWS Management Console to create a new connection. When requesting a connection, you will be asked to select a Direct Connect location, the number of ports, and the port speed. You work with a Direct Connect Partner if you need assistance extending your office or data center network to a Direct Connect location.
4.2 Proceed to order the Direct Connect connection
4.2.1 (Optional) Dedicated Direct Connect connections For dedicated Direct Connect connections, you must first request them through the AWS console, have it approved by AWS, and then order it through an AWS Partner or network provider.
4.2.2 (Optional) Hosted Direct Connect connections For hosted Direct Connect connections, you must order them through an AWS Partner and then accept in the AWS console.
4.3 Create Transit virtual interface Provide access to one or more AWS Transit Gateways.
For more detailed steps on configuring Direct Connect, refer to the AWS documentation.
5. Update Landing Zone Accelerator with Direct Connect connection ID
After ordering the Direct Connect (DX) connection and obtaining the physical connection ID (dxcon-xxxxxx), you will need to update the Landing Zone Accelerator configuration to integrate the Direct Connect connection into your landing zone.
5.1 Locate the networking configuration YAML file in your Landing Zone Accelerator deployment This is typically stored in an S3 bucket.
5.2 Add Direct Connect connection to Landing Zone Accelerator networking configuration In the networking configuration, find the section for Direct Connect connections and add the new Direct Connect connection ID.
5.3 Save the updated YAML file and commit the changes to your Landing Zone Accelerator configuration repository. Follow these steps if you are unfamiliar with updating the configuration files.
5.4 Deploy the updated Landing Zone Accelerator configuration to apply the changes and connect your landing zone to the new Direct Connect connection.
5.5 Update the Transit Gateway to accept the Direct Connect connection By updating the Landing Zone Accelerator configuration with the Direct Connect connection ID and associating it with the Transit Gateway, the solution will now be able to manage and maintain the necessary network resources, such as virtual interfaces, to establish a secure and reliable connection between your on-premises network and the RISE with SAP environment running on AWS.
For more information on updating the Landing Zone Accelerator configuration, refer to the official documentation
6. Configure your network’s customer gateway devices for Site-to-Site VPN and/or Direct Connect
6.1 Site-to-Site VPN Configuration After setting up the Site-to-Site VPN connection within the Landing Zone Accelerator, you will need to configure your corporate network customer gateway device to complete the VPN setup. Follow the documentation for configuring your device with either static or dynamic configuration files.
You’ll need to configure the VPN tunnels on your corporate network router. This includes setting up the following:
- Customer Transit Gateway ID
- Customer AWS Account ID
- Customer Network IP ranges (IP ranges used in customer VPC as well as on-premise if gateway transit is used)
6.2 Direct Connect configuration For the Direct Connect connection, you’ll need to focus on setting up the VLAN interface and BGP on your on-premises routers. Refer to the AWS documentation on router configuration for Direct Connect for the necessary settings.
Additionally, you’ll want to implement routing policies that prefer the Direct Connect connection over the VPN as the primary path. This can be achieved by configuring BGP communities or more specific subnet advertisements to influence the traffic flow from AWS to your on-premises network.
If you’re implementing an active/active VPN topology, you’ll need to:
- Configure your on-premises routers to handle multiple VPN tunnels
- Implement routing policies to balance traffic across the redundant VPN tunnels, again leveraging BGP communities or more-specific subnet advertisements
Refer to the AWS documentation on router configuration for Direct Connect for the necessary settings.
7. Configure Direct Connect and Site-to-Site VPN for failover
The document Configure Direct Connect and VPN failover with Transit Gateway on AWS re:Post provides an overview of the steps to configure the failover between the Direct Connect and Site-to-Site VPN connections.
The key steps involve attaching the Direct Connect and Site-to-Site VPN connections to the Transit Gateway managed by Landing Zone Accelerator, then, configuring the route tables to manage the failover routing. This creates reliable connectivity between your on-premises environment and the RISE with SAP deployment on AWS, with the Direct Connect connection as the primary link and the Site-to-Site VPN as the failover.
8. Connect to RISE with SAP environment
To establish the connection between your on-premises network and the RISE with SAP environment running on AWS, you’ll need to provide some key information to SAP:
- Customer Transit Gateway ID: This is the Transit Gateway that was configured within your Landing Zone Accelerator environment to manage the network connectivity.
- Customer AWS Account ID: This is the AWS account ID associated with the Landing Zone Accelerator environment where the TGW was provisioned.
- Customer Network IP Ranges: Provide the IP address ranges used in your customer VPC(s) within the Landing Zone Accelerator.
You’ll need to fill out the SAP Connectivity Questionnaire and share these details with the SAP ECS Delivery team. This allows SAP to properly route traffic between your on-premises network and the RISE with SAP deployment running on AWS.
By providing this information, you’ll enable the network connectivity required for your users to access the SAP services and applications hosted in the cloud.
9. (Optional) Configure network traffic monitoring with AWS Network Firewall
The Landing Zone Accelerator allows you to centrally manage and enforce network security controls across your AWS environment using Network Firewall. This ensures consistent network security policies are applied to all your VPCs, including the ones used for your RISE with SAP deployment.
9.1. Create AWS Network Firewall configuration in the Landing Zone Accelerator In the Landing Zone Accelerator networking configuration YAML file, create a network-firewall section.
9.2. Customize the firewall policy and rules Modify the firewallRules section to match your specific security requirements for the RISE with SAP environment. For example, you may want to add rules to allow access to specific SAP services and ports, or to restrict access from untrusted IP ranges.
9.3. Associate the Network Firewall policy with your VPCs and Transit Gateway In the resourceSetup section, update the resourceArns to include the VPC IDs for the VPCs hosting your RISE with SAP deployment, as well as the Transit Gateway ID.
9.4. Deploy the updated Landing Zone Accelerator configuration After making the changes, save the YAML file and deploy the updated Landing Zone Accelerator configuration. This will create the Network Firewall and associate it with the specified VPCs and Transit Gateway, ensuring consistent network security enforcement for your RISE with SAP environment.
Testing the Guidance
To ensure the network connectivity and security controls are functioning as expected, you’ll need to perform thorough testing of the Guidance.
AWS Direct Connect
Coordinate with your network team to enable the BGP sessions for the Direct Connect connections. Verify the BGP paths and test failover scenarios by simulating the failure of one connection to ensure traffic is properly rerouted.
Confirm end-to-end connectivity between your on-premises environment and the AWS resources provisioned by the Landing Zone Accelerator. You can also leverage the AWS Direct Connect Resiliency Toolkit to perform scheduled failover tests and verify the resiliency of your connections.
AWS Site-to-Site VPN
Coordinate with your network team to enable the Site-to-Site VPN connection and verify end-to-end connectivity. Test failover scenarios by simulating a Direct Connect failure and ensure traffic properly fails over to the VPN.
Confirm that the failover is working as expected for both the Direct Connect and VPN paths.
AWS Network Firewall
Validate the AWS Network Manager policies and rules by testing various traffic flows between your on-premises network and the resources in the Landing Zone Accelerator environment. Confirm that the expected security controls are being enforced, such as allowed/denied protocols, ports, and IP ranges.
AWS Transit Gateway
Test the integration between the Transit Gateway, Direct Connect, and VPN connections by sending traffic from your on-premises network to resources in the Landing Zone Accelerator environment. Confirm that the traffic is properly routed through the Transit Gateway and inspected by the AWS Firewall Manager policies.
Simulate failure scenarios, such as a Direct Connect outage, and verify that traffic seamlessly fails over to the VPN connection without impacting the resources in the Landing Zone Accelerator environment.
Maintaining the Guidance
For detailed instructions on updating the Landing Zone Accelerator configuration, including the networking and connectivity settings, refer to the official documentation.
The Landing Zone Accelerator configuration is managed through YAML files, allowing you to easily make changes to the networking, security, and other settings as needed. The documentation outlines the step-by-step process for updating the Landing Zone Accelerator configuration and deploying the changes.
How to stay up to date (git):
- Fork the Landing Zone Accelerator GitHub repository: https://github.com/awslabs/landing-zone-accelerator-on-aws
- Create a branch for your changes:
git checkout -b my-updates - Make the necessary changes to the YAML configuration files
- Commit and push your changes to your forked repository:
git add . git commit -m "Update LZA configuration" git push origin my-updates \``` - Monitor the Landing Zone Accelerator repository for updates and periodically merge the upstream changes into your forked repository.
- Regularly review and update the configurations for both the Direct Connect and VPN connections. Coordinate any changes with SAP.
Uninstall the Guidance
If you need to uninstall or remove the Landing Zone Accelerator and associated resources, please follow the steps provided in the official Landing Zone Accelerator documentation.
This guide covers the necessary steps to cleanly remove the Landing Zone Accelerator and its associated resources from your AWS environment.
Contributors and Revisions
- Zach Daniels
- Rozal Singh
- Adam Hill
Notices
Customers are responsible for making their own independent assessment of the information in this document. This document: (a) is for informational purposes only, (b) represents AWS current product offerings and practices, which are subject to change without notice, and (c) does not create any commitments or assurances from AWS and its affiliates, suppliers or licensors. AWS products or services are provided “as is” without warranties, representations, or conditions of any kind, whether express or implied. AWS responsibilities and liabilities to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.