Guidance for Multi Account Outposts Operations on AWS
Summary: This implementation guide provides an overview of the Guidance for Multi Account Outposts Operations on AWS, its reference architecture and components, considerations for planning the deployment, and configuration steps for deploying the Guidance. This guide is intended for solution architects, business decision makers, DevOps engineers, Data Scientists, and Cloud professionals who want to implement Guidance for Multi Account Outposts Operations on AWS in their environment.
Overview
AWS Outposts is a fully managed service that extends AWS infrastructure, services, APIs, and tools to customer premises. By providing local access to AWS managed infrastructure, AWS Outposts enables customers to build and run applications on premises using the same programming interfaces as in AWS Regions, while using local compute and storage resources for lower latency and local data processing needs.
An Outpost is a pool of AWS compute and storage capacity deployed at a customer site. AWS operates, monitors, and manages this capacity as part of an AWS Region.
In many scenarios the AWS Outposts rack is shared across multiple application teams/stakeholders that use the rack to host their workloads and also consume services that are offered on the Outposts rack. In such deployments, an Outposts rack is shared to different AWS accounts under the same AWS Organization allowing effective use of the Outpost in a shared environment. These use-cases span various sectors including telecom, digital services, financial sector, and enterprise where organizations needed a solution to effectively manage shared Outpost resources. This guidance provides a comprehensive management of multi-account AWS Outposts deployments, enabling organizations to effectively share Outpost resources across multiple Consumer accounts while maintaining control and visibility over resource utilization.
This guidance aims to instruct and guide users on how to monitor account level resource utilization and enforce soft and hard limits on Outposts rack EC2 instances on member accounts that share the Outposts rack.
Features and benefits
This guidance provides the following features:
Monitoring
The guidance uses two approaches to monitor the AWS Outposts rack.
The first one is defining Amazon CloudWatch alerts on relevant CloudWatch metrics. For example, we have a metric that shows Amazon Simple Storage Service (Amazon S3) usage on the Outpost per consumer account. An alert definition might then be “trigger when consumer A exceeds 10TiB usage”. This alert will create an event in the guidance that we can use to start an intervention. It also use metrics and alerts to display a dashboard in CloudWatch detailing many aspects of consumer resource usage.
The second approach to monitoring is using AWS service events. One of the services emitting such events is Amazon Elastic Compute Cloud (Amazon EC2). Whenever an EC2 instance transitions into another state, an event like “Instance i-123456789 has gone into pending” is generated. The guidance uses Amazon EventBridge to capture such events and route them from the consumer account into the owner account.
For customers looking into observability and monitoring insights both at the consolidated Outposts level and at individual AWS accounts level, this guidance offers one unified dashboard to view aggregated metrics.
Intervening
The guidance takes two approaches to interventions that work hand-in-hand. First, we use AWS Identity and Access Management (IAM). The guidance assumes that every consumer accesses their AWS account through a well- defined IAM role. That role must be made known to the guidance, otherwise it will create a role in the consumer account.
An IAM based intervention then involves taking away relevant permissions from that role. For example, if too many EC2 instances have been launched, the permissions are altered such that no further instances can be launched for that specific consumer AWS account.
The second approach of this guidance is deleting resources that are above the threshold. For example, when the guidance detects that too many EC2 instances are running in a consumer account, the most recently launched ones will be terminated. The guidance implements CloudWatch and IAM based monitoring and intervention for various services. Service Events with IAM and Termination is only implemented for EC2 on Outposts rack.
For customers looking to enforce quotas with soft and hard limits, the guidance’s web UI provides a mechanism of setting limits at both the consolidated outposts level and also to individual member AWS accounts that share the Outposts rack. This is really helpful in B2B/B2G use-cases where the Outpost owner might want to strictly enforce hard limits on EC2 instances for member accounts.
Architecture
Architecture diagram
This section provides architecture diagrams and describes the components deployed with this Guidance.
Architecture of Guidance for Multi Account Outposts Operations on AWS
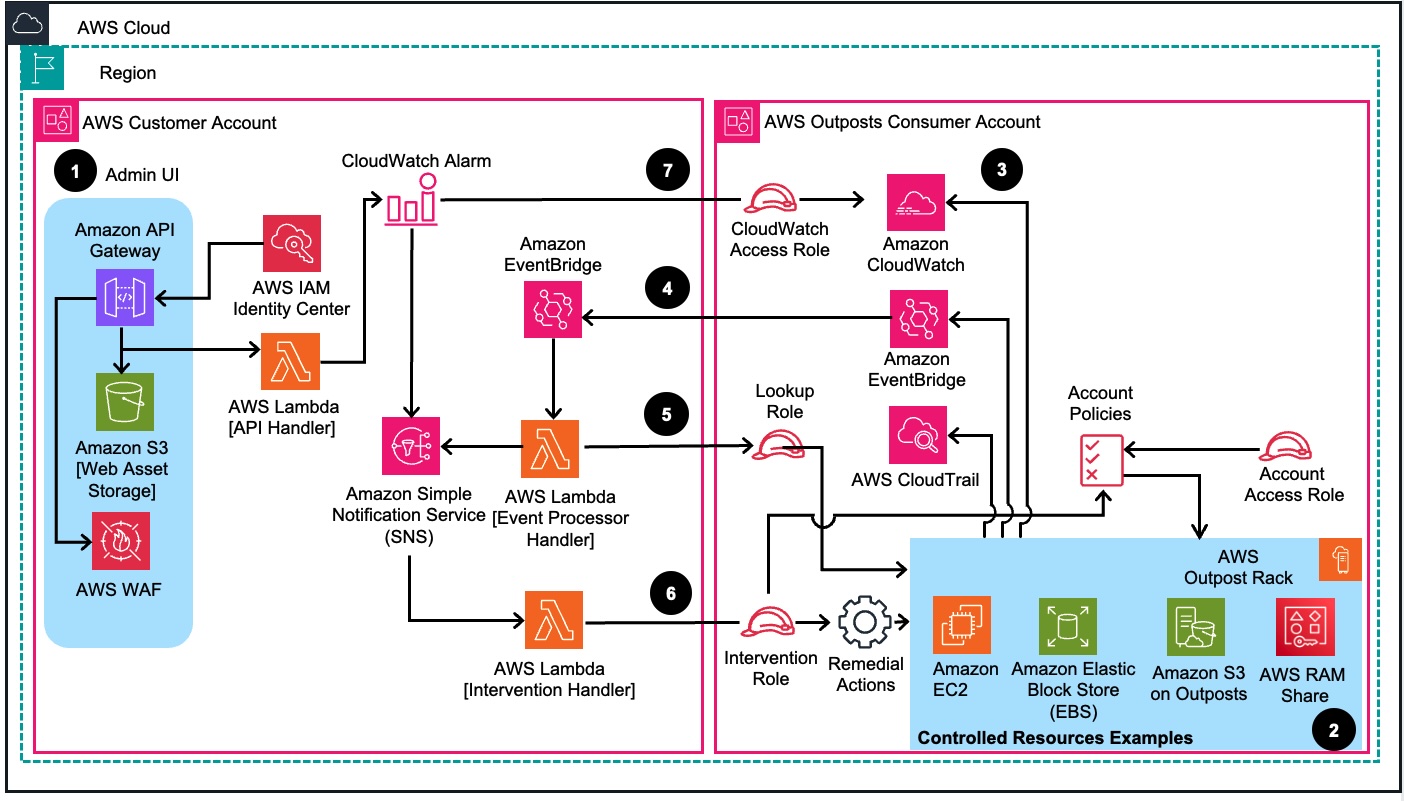
Figure 1: Multi Account Outposts Operations on AWS Reference Architecture
Architecture steps
- The guidance is integrated with AWS IAM Identity Center for authentication purposes. The web UI is hosted in the AWS Account of the AWS Outposts owner account and hosted API using AWS API Gateway, with AWS Web Application Firewall (WAF) for IP-based access control. The AWS Lambda API handler executes changes in the UI.
- AWS Outposts rack is shared with Consumer AWS account using AWS Resource Access Manager (RAM). Controlled resources on the Outposts rack such as Amazon EC2, Amazon EBS and Amazon S3 on Outposts are available.
- Alert thresholds are directly read from and written to the Amazon CloudWatch alert configuration. The guidance uses the CloudWatch access role to view and read the alert definitions in the consumer account.
- The Event management system is based on AWS EventBridge and operates by routing AWS service notifications (for example: “an EC2 instance has started”)
- This event invokes the ’Event Processing’ Lambda function and via the LookupRole and retrieves up-to-second accurate usage data from the Consumer account. The Lambda also reads all relevant alert settings from CloudWatch and makes a decision on whether an intervention should occur.
- The Event Processing Lambda then sends a message on the Amazon SNS Alert Topic to the ‘Intervention Handler’ Lambda function, which performs remedial actions as applicable.
- The CloudWatch alert-based system is triggered directly by CloudWatch when an alerting level is crossed.
AWS services in this Guidance
| AWS Service | Role | Description |
|---|---|---|
| AWS EventBridge | Core service | Routes operational events and notifications for Outposts resources |
| AWS Lambda | Core service | Executes event processing and intervention handling for automated remediation |
| Amazon CloudWatch | Core service | Monitors resources and manages alert configurations for capacity management |
| AWS IAM Identity Center | Core service | Manages user authentication and access control for the web UI |
| Amazon SNS | Core service | Handles message delivery between Event Processing and Intervention Handler Lambda functions |
| AWS API Gateway | Supporting service | Hosts APIs and routes requests from web UI to Lambda handlers |
| AWS WAF | Supporting service | Provides IP-based access control for the web interface |
| AWS RAM | Supporting service | Enables resource sharing between owner and consumer accounts |
| IAM Roles | Supporting service | Manages cross-account permissions and access controls |
| Amazon S3 | Supporting service | Hosts web UI static content |
| Amazon EC2 on Outposts | Supporting service | Managed resource on Outposts rack |
| Amazon EBS on Outposts | Supporting service | Managed resource on Outposts rack |
| Amazon S3 on Outposts | Supporting service | Managed resource on Outposts rack |
Cost
You are responsible for the cost of the AWS services used while running this guidance. As of May 2025, the cost for running this guidance with the default settings in the US WEST (Oregon) Region is approximately $98.50/month. We recommend creating a budget through AWS Cost Explorer to help manage costs. Prices are subject to change. For full details, refer to the pricing webpage for each AWS service used in this guidance.
Multi Account Outposts Operation Guidance Cost
The following table provides a sample cost breakdown for deploying this guidance with the default parameters in the us-east-1 (N. Virginia) Region for one month. This estimate is based on the AWS Pricing Calculator output for the full deployment as per the guidance.
Note: The following cost table does not include the cost of using the AWS Outposts rack. Customers will have to procure an Outpost rack inorder to deploy this guidance.
| AWS service | Dimensions | Cost, month [USD] |
|---|---|---|
| AWS Lambda | Event Processing & Intervention Handler: 100,000 invocations/month, 512MB memory, 500ms avg duration | 20.00 |
| Amazon CloudWatch | 25 custom metrics, log storage 10GB, API requests | 30.00 |
| AWS API Gateway | 1M API calls/month, 1 API, data transfer 50GB | 35.00 |
| Amazon SNS | 100,000 messages/month, standard topic | 0.50 |
| AWS EventBridge | 1M custom events/month, 1 event bus | 1.00 |
| AWS WAF | 1 web ACL, 2 rules, 1M requests/month | 7.00 |
| Amazon S3 | Web UI static content: 1GB storage, 100K requests | 0.50 |
| AWS IAM Identity Center | User authentication and management | free |
| AWS Resource Access Manager | Resource sharing between accounts | free |
| Amazon Virtual Private Cloud (VPC) | 1 VPC, 2 subnets, data transfer 50GB | 4.50 |
| TOTAL | 98.50 |
For a more accurate estimate based on your specific configuration and usage patterns, we recommend using the AWS Pricing Calculator.
Security
When you build systems on AWS infrastructure, security responsibilities are shared between you and AWS. This shared responsibility model reduces your operational burden because AWS operates, manages, and controls the components including the host operating system, the virtualization layer, and the physical security of the facilities in which the services operate. For more information about AWS security, visit AWS Cloud Security
Data Access
- Ensure only authorized personnel have access to the data. Follow the Official AWS IAM Security Best Practices when creating and giving access to users in the AWS Account
- Scoping least-privilege permissions can be simplified using
- IAM policy simulator to test the effect of policy changes
- IAM Access Analyzer to generate an IAM policy for an entity based on its access
Amazon S3
AWS Lambda
Amazon Elastic Compute Cloud (Amazon EC2)
AWS Outposts
NodeJS
Supported AWS Regions
This Guidance uses the AWS Outposts service, which is not currently available in all AWS Regions. You must launch this guidance in an AWS Region where AWS Outposts is available. For the most current availability of AWS services by Region, refer to the AWS Regional Services List
Please note that this guidance is applicable to First Generation of Outposts rack. While the intended functionality should not differ for the Second Gen Outposts rack, customers are advised to conduct detailed validation prior to its implementation.
Multi Account Outposts Operations Guide is supported in the following AWS Regions for the First Generation of Outposts racks:
| Region Name | |
|---|---|
| US East (Ohio) | AWS GovCloud (US-West) |
| US East (N. Virginia) | AWS GovCloud (US-East) |
| US West (Northern California) | Middle East (Bahrain) |
| US West (Oregon) | Middle East (UAE) |
| Canada (Central) | Israel (Tel Aviv) |
| South America (São Paulo) | Africa (Cape Town) |
| EU (Frankfurt) | Asia Pacific (Singapore) |
| EU (Stockholm) | Asia Pacific (Sydney) |
| EU (Ireland) | Asia Pacific (Jakarta) |
| EU (Milan) | Asia Pacific (Tokyo) |
| EU (Spain) | Asia Pacific ( Seoul ) |
| EU (London) | Asia Pacific (Osaka) |
| Europe (Paris) | Asia Pacific (Mumbai) |
Deploy the Guidance
Prerequisites
An AWS Outpost environment configured with:
- One account
- Called the Customer account
- Owns the Outpost
- One or more accounts
- Called the Consumer accounts
- Share their Amazon CloudWatch metrics with the Customer account
Before starting the deployment, ensure you have:
- Administrative access to all three AWS accounts (Customer/Owner account and both Tenant accounts)
- Node.js version 18-22 installed
- pnpm package manager installed
- AWS CLI v2 installed and configured
- Access to AWS IAM Identity Center (AWS SSO) for all accounts
Required IAM Permissions
Each account requires a user/role with AdministratorAccess or equivalent permissions including:
- IAM role/policy management
- CloudFormation stack operations
- Cross-account trust relationship setup
- All AWS services used by the solution (CloudWatch, Lambda, API Gateway, WAF, etc.)
Deployment process overview
Before you launch the Guidance, review the cost, architecture, security, and other considerations discussed in this guide. Follow the step-by-step instructions in this section to configure and deploy the Guidance into your account.
Time to deploy: Approximately 1 hour
Deployment Steps
Set up IAM Identity Center
Before configuring the AWS CLI with SSO, you need to set up IAM Identity Center to get the SSO start URL:
- Log in to the AWS Console of the Customer account
- Navigate to IAM Identity Center
- Enable IAM Identity Center if not already enabled. This will create an organization and add the current account to it
- Set the Identity Source to Identity Center directory if it already hasn’t.
- Note the AWS access portal URL (this will be your SSO start URL for the next step)
Configure AWS Command Line Interface (CLI)
- Enter the following within a terminal
aws configure ssoNext enter the AWS IAM Identity Center (successor to AWS Single Sign-On) start URL and region for the Outpost to which the guidance is to be deployed. For example
SSO Region [None]: eu-west-2 SSO start URL [None]: https://foooutpost.awsapps.com/startThe tool will attempt to open the authorization page in the browser
SDDD-GFRD Attempting to automatically open the SSO authorization page in your default browser.
If the browser does not open or you wish to use a different device to authorize this request, open the following URL: https://device.sso.eu-west-2.amazonaws.com Then enter the code: FOO-BAR
Within the browser page, enter the username and password registered for the Outpost and wait for a verification code to be emailed to you from no-reply@login.awsapps.com
Enter the code in the web page, to use an MFA device such as fingerprint scanner in place of the emailed verification code
- Click MFA Devices at the top of the page
- Select the MFA device to use, eg
- Fingerprint scanner
- Authy desktop
- Yubikey
- Follow the steps in the browser to register the device
The terminal will then allow you to select an account Select the Customer account; for example
There are 3 AWS accounts available to you.
> Customer, customer@foo.com (111111111)
ConsumerA, consumerA@bar.com (222222222)
ConsumerB, consumerB@bar.com (333333333)
Using the account ID 111111111
The only role available to you is: CustomerAccess
Using the role name "CustomerAccess"
CLI default client Region [eu-west-2]:
CLI default output format [None]:
CLI profile name [CustomerAccess-111111111]:
To use this profile, specify the profile name using –profile, as shown:
aws s3 ls --profile CustomerAccess-11111111
This will create an entry for the account within ~/.aws/config. For example
[profile CustomerAccess-111111111]
sso_start_url = https://foooutpost.awsapps.com/start
sso_region = eu-west-2
sso_account_id = 111111111
sso_role_name = CustomerAccess
region = eu-west-2
Repeat the above steps for each Consumer account
- Clone the sample code repository to your local machine:
Set an environment variable named PROJECT_HOME to the root directory of the guidance For example, on a Unix system using zsh
❯ pwd
/Users/foo/Documents/code/AWS-Multi-Account-Outposts
❯ export PROJECT_HOME=/Users/foo/Documents/code/AWS-Multi-Account-Outposts
Configure guidance Stage
The guidance can be deployed to multiple stages, such as production and testing. For each stage, create a configuration file in settings/lib/stages/<stage_name>.ts
For example, a newly created settings/lib/stages/testing.ts file might contain the following (with values replaced for the specific customer/deployment):
import { IApplicationConfig, EnvType } from '../models/application-interface.config';
const config: IApplicationConfig = {
awsRegion: 'eu-west-2',
awsProfile: 'CustomerAccess-111111111',
awsAccount: '111111111',
awsEmail: 'customer@foo.com',
tenantAwsAccounts: [
{ account: '*********', profile: 'TenantAccess-*********', email: 'tenantA@bar.com' },
{ account: '333333333', profile: 'TenantAccess-333333333', email: 'tenantB@bar.com' },
],
solutionName: 'multiacc',
solutionFullName: 'MultiTenant Outpost',
envType: EnvType.Dev,
outpostConfig: {
instanceFamilies: ['M5', 'R5'],
ec2Types: ['m5.xlarge', 'r5.2xlarge'],
volumeTypes: ['gp2'],
accountIds: ['*********', '*********'],
outpostId: 'op-11111111111111',
},
outpostAvailabilityZone: 'eu-west-2a',
samlCert: '',
samlEntryPoint: '',
samlLogoutUrl: '',
ec2InterventionMode: 'terminate',
};
export default config;
Optional: A stage config can also be stored in AWS Systems Manager Parameter Store to prevent undesired exposure of account ids and emails. A JSON serialization of the config object is stored in the Parameter Store in the owner’s account, and the name of the store is provided instead of the full config, as shown below. You need to login to the owner’s account with the AWS Command Line Interface (AWS CLI) before deploying the guidance this way.
import { IStageConfig } from '../models/application-interface.config';
const config: IStageConfig = {
// requires aws account credential, region and key to read config from SSM
useRemoteConfig: 'stage-config-outpost-demo',
};
export default config;
Optional: Configure CICD pipeline
If any code artifact repository is referenced in the CICD pipeline then within Configure guidance Stage include values for
// AWS Account ID for the Code Artifact repository
codeArtifactAccountId?: string;
// Domain of CodeArtifact repository
codeArtifactDomain?: string;
// Name of CodeArtifact repository
codeArtifactRepository?: string;
// AWS Region for CodeArtifact resources
codeArtifactRegion?: string;
// Namespace of NPM packages to be pulled
codeArtifactNamespace?: string;
Deploy guidance Stage
Configure AWS CLI for the Customer account, then deploy the guidance stage:
cd $PROJECT_HOME/cli
pnpm --version
pnpm install
pnpm cli deploy --stage testing
Validate before running if needed
pnpm -r compile
After about twenty minutes deployment will be complete and the API endpoint, web URL and SAML data will be reported
┌───────────────┬────────────────────────────────────────────────────────────┐
│ API Endpoint │ https://aaa-bbb.execute-api.eu-west-2.amazonaws.com/testing/ │
│ Web URL │ https://aaa-bbb.execute-api.eu-west-2.amazonaws.com/testing/ │
│ SAML ACS URL │ │
│ SAML audience │ │
└───────────────┴────────────────────────────────────────────────────────────┘
Keep a note of this endpoint and the URL, you will need them for the next steps.
Troubleshooting
Prerequisites Verification Check
Confirm that the correct versions of the Prerequisites are installed and reinstall/update if necessary:
node --version # should be ≥20.11.1
aws --version # should be ≥2.15.45
cdk --version # should be ≥2.137.0
pnpm --version # should be ≥8.15.6
SSO and Credential Issues
Problem: CredentialsProviderError: Could not load credentials from any providers
Solutions:
- Refresh SSO sessions (sessions expire every few hours):
aws sso login --profile AdministratorAccess-acct-id - Set AWS_PROFILE environment variable:
export AWS_PROFILE=AdministratorAccess-acct-id - Use temporary credentials if SSO keeps failing:
aws configure export-credentials --profile AdministratorAccess-acct-id --format env # Copy and paste the export commands unset AWS_PROFILE # Remove profile to use temp credentials
Problem: UnauthorizedException: Session token not found or invalid
Solution: Your SSO session has expired. Re-login:
aws sso login --profile AdministratorAccess-acct-id
CloudFormation Permission Issues
Problem: User: arn:aws:sts::ACCOUNT:assumed-role/cdk-cb9e0039b0-cfn-exec-role-ACCOUNT-REGION/AWSCloudFormation is not authorized to perform: cloudwatch:PutMetricAlarm
Root Cause: The CloudFormation execution role lacks necessary permissions.
Solution: Update the CloudFormation execution policy to have full permissions:
# Attach AdministratorAccess to the CloudFormation execution role
aws iam attach-role-policy --role-name cdk-cb9e0039b0-cfn-exec-role-acct-id-us-east-1 --policy-arn "arn:aws:iam::aws:policy/AdministratorAccess"
# Wait 2-3 minutes for IAM propagation, then retry deployment
Cross-Account Role Assumption Issues
Problem: Could not assume role in target account using current credentials
Cause: Tenant accounts aren’t properly bootstrapped or trust relationships are missing.
Solution: Re-bootstrap the tenant accounts with proper trust:
# For each tenant account, set its credentials and run:
pnpm cdk bootstrap aws://TENANT_ACCOUNT_ID/us-east-1 --trust acct-id --toolkit-stack-name "dev-va-multiten-toolkit" --qualifier "cb9e0039b0" --cloudformation-execution-policies "arn:aws:iam::aws:policy/AdministratorAccess"
AWS CLI Configuration
Confirm that the AWS CLI has been configured correctly by executing the following command:
aws --profile <PROFILENAME> s3 ls
If this does not return a list of S3 buckets, or there are any errors, then repeat the steps in Configure AWS Command Line Interface (AWS CLI)
Verify AWS STS Identity
Verify aws sts get-caller-identity for all accounts from your CLI. This will ensure correct working of the profiles and the Identity Center:
aws sts get-caller-identity --profile CustomerAccess-111111111
aws sts get-caller-identity --profile TenantAccess-222222222
aws sts get-caller-identity --profile TenantAccess-333333333
AWS Users Setup
If undertaking the steps in Configure AWS Command Line Interface (AWS CLI) does not resolve the issue then setup the users manually through Console:
aws configure --profile <PROFILENAME>
Common Deployment Errors
Error: InvalidClientTokenId: The security token included in the request is invalid.
When you deploy the guidance using pnpm cli deploy, please re-login with SSO using this command for the outpost owner profile:
aws sso login --profile customer-access
If you are still not able to resolve the token issues, you can always create a user in the customer account and export the access ID, secret access key and the session token for this user and run the above command.
Error: cfn-exec-role is not authorized to perform cloudwatch:putmetricalarm
Please verify the inline permission policies of the cfn-exec-role in the customer account. The policies of this account will be used to create resources in the consumer accounts as well.
Steps in the AWS Console
Log in to the AWS Console of the account that hosts the IAM Identity Center instance. In the context of AWS Outposts, this may be the Customer account, but it can be any account. It does not have to be the same account as where the guidance is deployed.
Setting up AWS IAM Identity Center Authentication
Configure Guidance UI as a SAML Service Provider
- In the IAM Identity Center console, under Applications, select Add Application. Select Add Custom SAML 2.0 application and click Next.
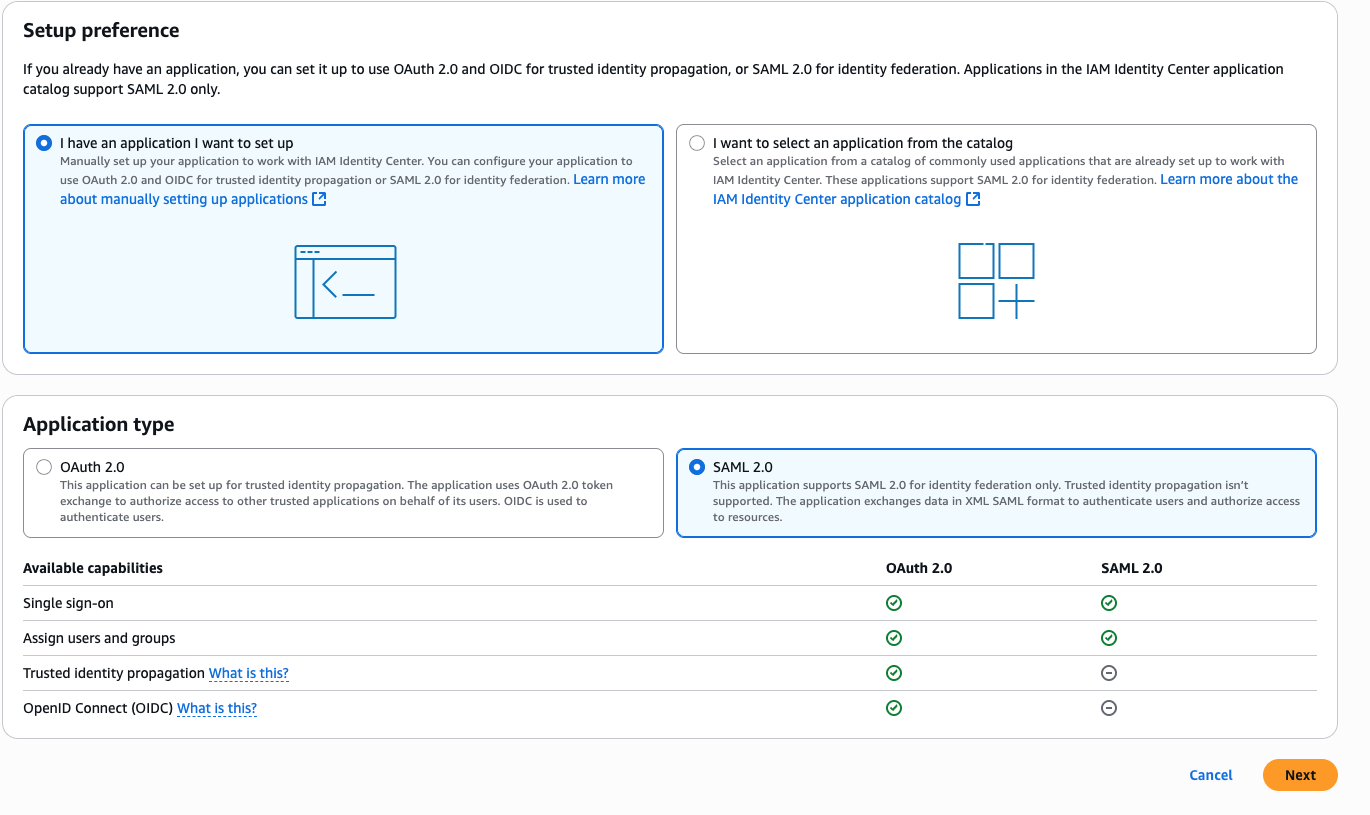
Figure 2: Add SAML application
- Give the application a name and a description.
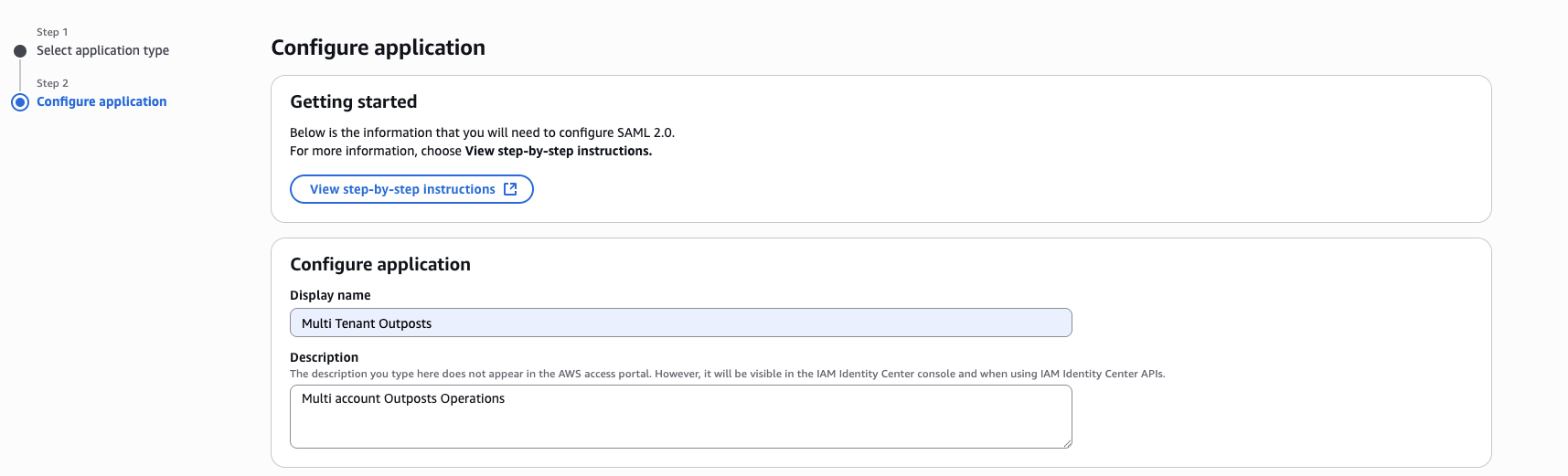
Figure 3: Configure SAML Application Details
- Make a note of the displayed IAM Identity Center sign-in and sign-out URLs, under IAM Identity Center Certificate click Download to download the certificate.
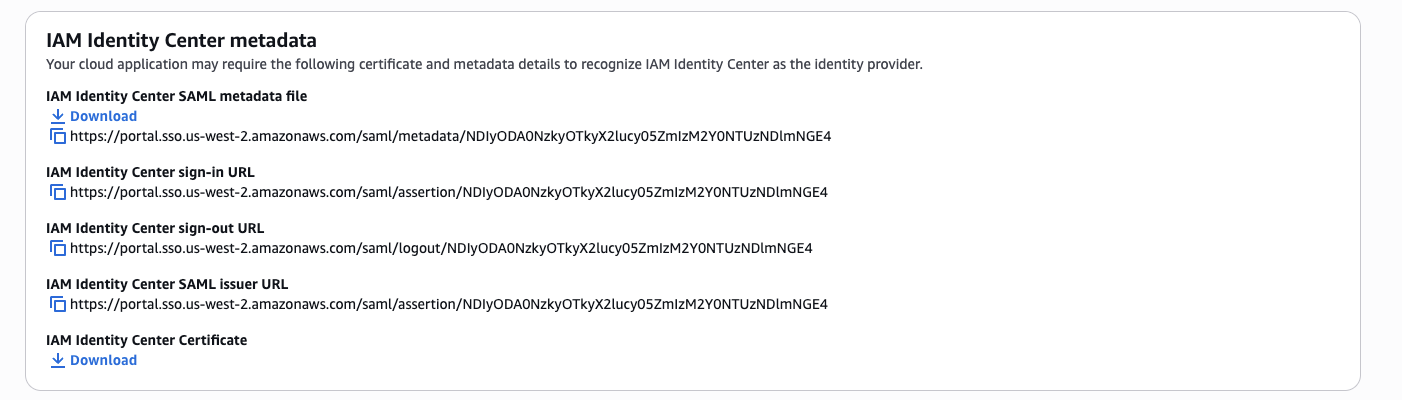
Figure 4: Identity Center Metadata
- Ignore the Application Properties section, Under Application Metadata select Manually type your metadata values and set
- Application ACS URL to the API endpoint for the deployed guidance (see Deploy guidance Stage) with /api/auth/saml/ac appended
- Application SAML audience to an appropriate or placeholder value
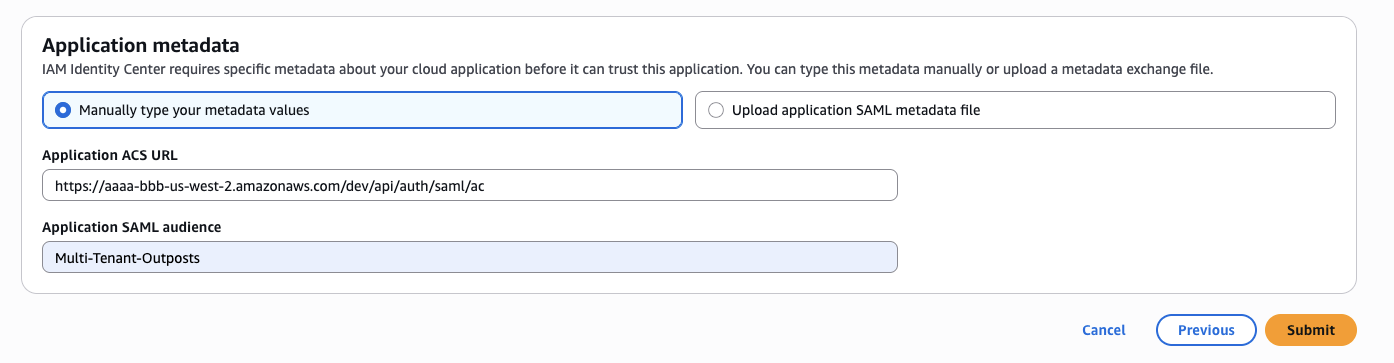
Figure 5: Application Metadata Config
- Click
Submit
Create a SSO user and associate it with the SAML app
- Open Users within the IAM Identity Center, Click Add User, Enter the user details for the Customer.
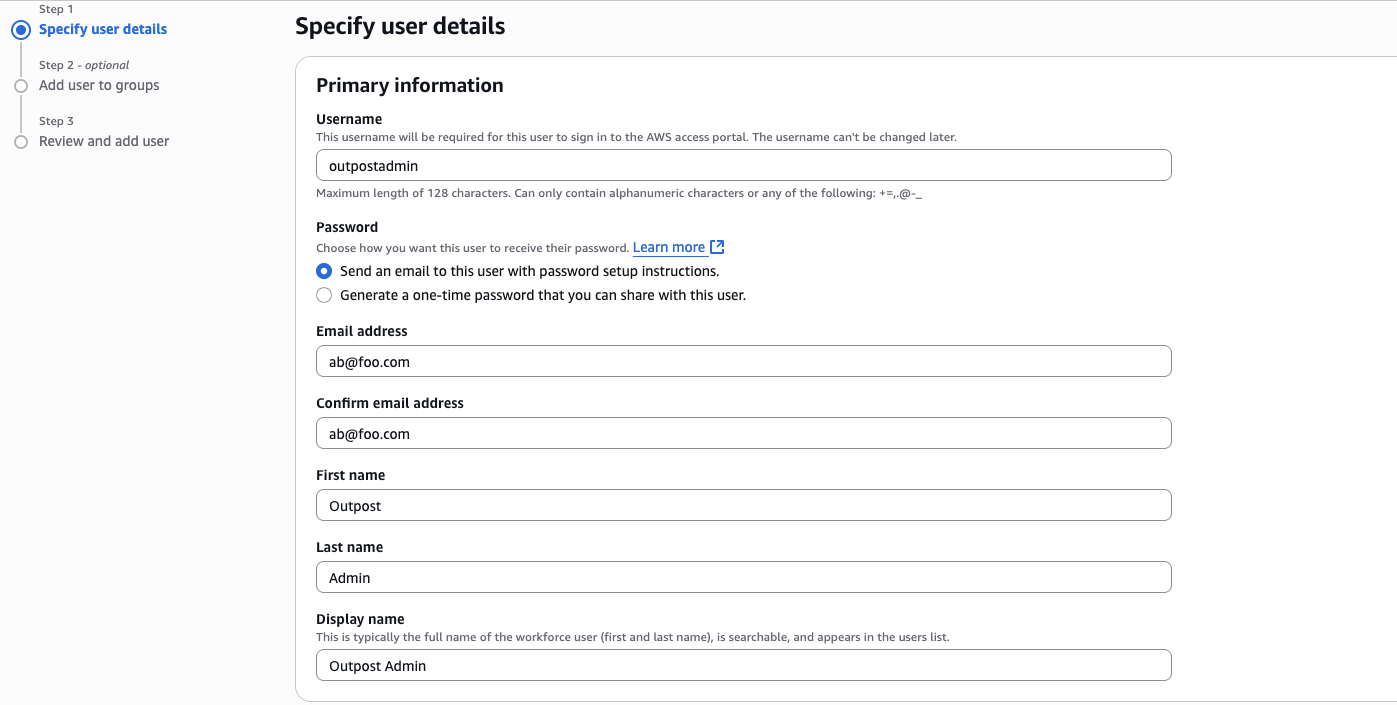
Figure 6: Adding a SSO user
- Click
Next, ClickNext, ClickAdd User
Associate the Customer with the SAML Application
- Open Applications within the IAM Identity Center
- Click the newly created application
- Click Assign Users
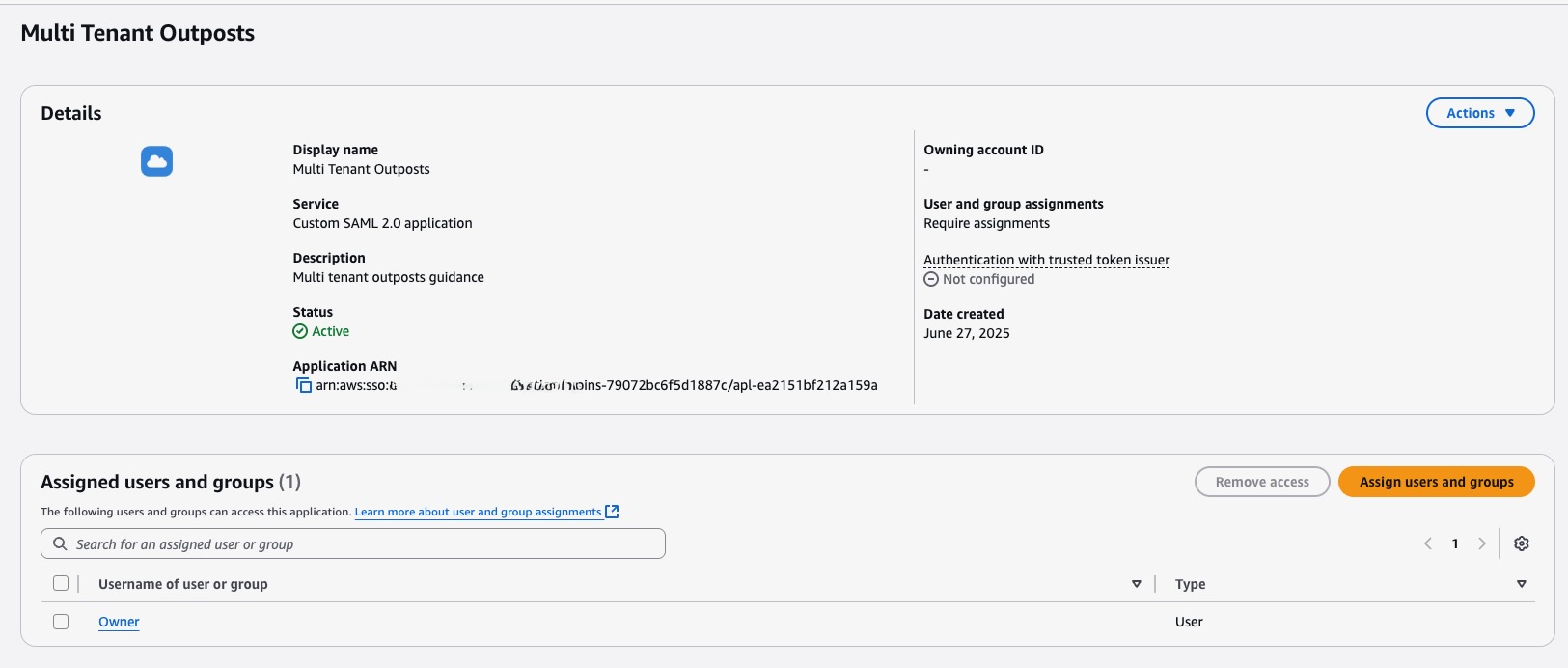
Figure 7: User Assignment
- Select the Customer user created earlier
- Click
Assign Users
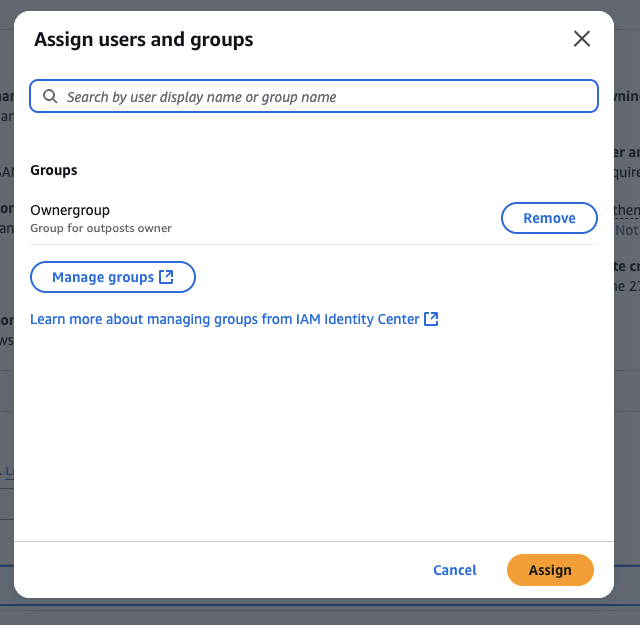
Figure 8: Selecting the User for assignment
Create an attribute mapping
- Open Applications within the IAM Identity Center
- Click the newly created application
- Click Actions, Edit attribute mappings
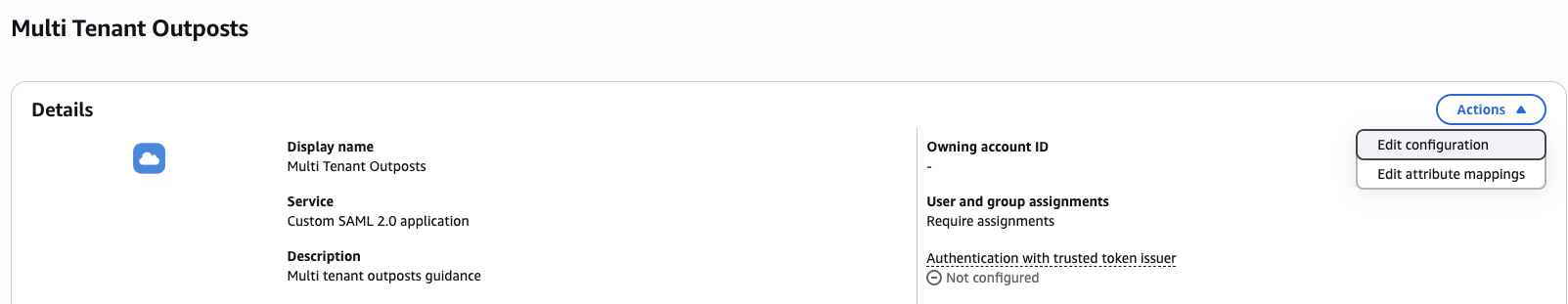
Figure 9: Edit attribute mappings
- Create the following mappings:
| User attribute | Maps to | Format |
|---|---|---|
${user:subject} | Subject | transient |
| admin | role | basic |
${user:givenName} | given_name | basic |
${user:familyName} | family_name | basic |
${user:email} | basic |
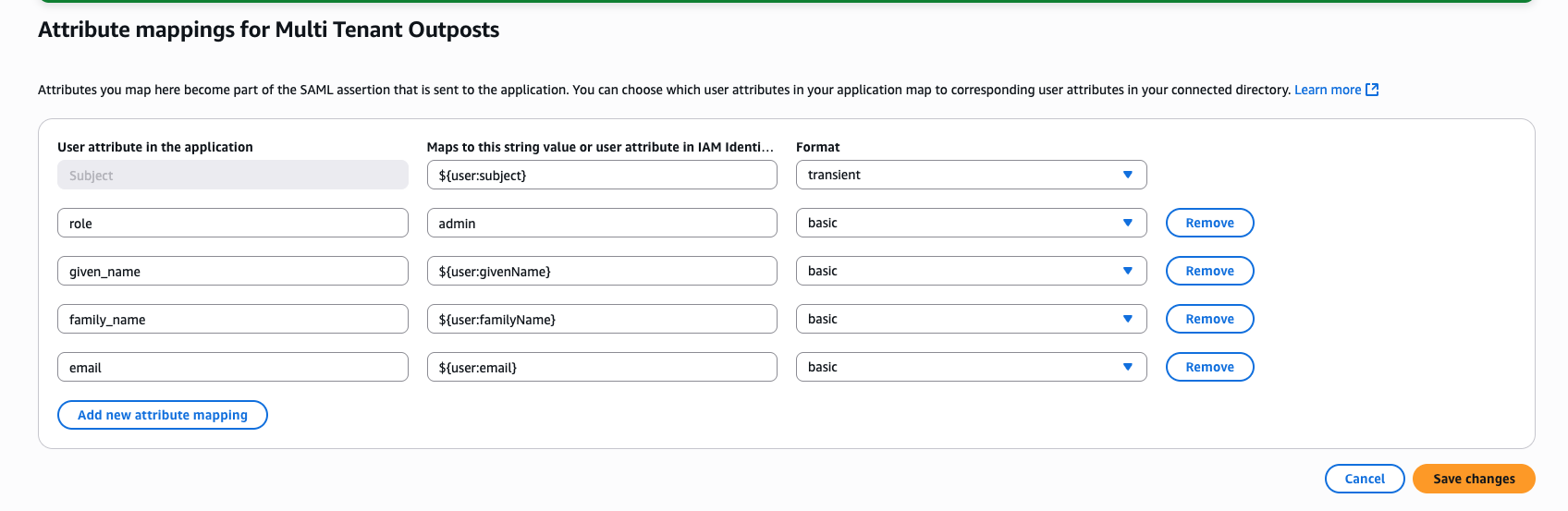
Figure 10: Attribute Mappings Config
- Click
Save Changes
Edit IAM Identity Center Certificate
Open the IAM Identity Center Certificate (downloaded in Configure guidance UI as a SAML Service Provider) in a text editor and delete
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
#All line breaks
For example, a downloaded certificate looks like:
-----BEGIN CERTIFICATE-----
foo
bar
-----END CERTIFICATE-----
Would become
foobar
Configure Solution Stage
Edit the guidance stage configuration file (configured in Configure guidance Stage) located at /settings/lib/stages/<stage_name>.ts and set
- samlCert to the edited IAM Identity Center Certificate (see Edit IAM Identity Center Certificate)
- samlEntryPoint and samlLogoutUrl to the IAM Identity Center sign-in/sign-out URLs recorded earlier (see
Configure Guidance UI as a SAML Service Provider)
For example, edit the file /settings/lib/stages/testing.ts to update the SAML configuration values:
const config: IApplicationConfig = {
// ... other configuration
samlCert: 'your_edited_certificate_here',
samlEntryPoint: 'https://your-identity-center-url/saml/assertion/abc123',
samlLogoutUrl: 'https://your-identity-center-url/saml/logout/abc123',
// ... rest of configuration
};
Deploy the solution stage:
cd $PROJECT_HOME/cli
pnpm --version
pnpm install
pnpm cli deploy --stage testing
Validate before running if needed:
pnpm -r compile
After about twenty minutes deployment will be complete and the API endpoint, web URL and SAML data will be reported.
- Signing into the UI
Open Dashboard within the IAM Identity Center and click the link under the AWS access portal URL to open the guidance
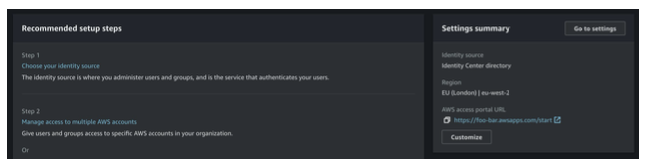
Figure 11: Signing into the UI
Using the Guidance
- Sign into the UI
- Resource constraints : Click Resources to open the page controlling Outpost and Consumer resources
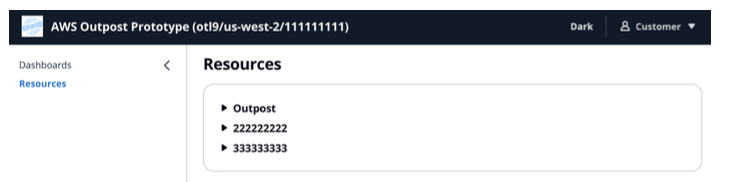
Figure 12: Accessing the Outpost and Consumer resources
- Click Outpost or any of the Consumer headings to edit their resources
Note: Consumer accordions may be empty unless an EC2 instance is created in a consumer account to create the data structure.
You may need to share VPC with consumer accounts as well.
- Outpost Resources : The guidance supports management of Outpost resources of type :
- Amazon Elastic Compute Cloud (Amazon EC2)
- Amazon Elastic Block Store (Amazon EBS)
- Amazon Simple Storage Service (Amazon S3)
Two thresholds may be set for each resource:
- Soft Limit
- When the total resource usage within the Outpost breaches this threshold an email is sent to the Customer
- Hard Limit
- When the total resource usage within the Outpost breaches this threshold all consumers are prevented from creating new resources of this type
- When the total resource usage within the Outpost falls below this threshold all Consumers are allowed to create new resources of this type, unless they are prevented from doing so by Consumer level thresholds
- Outposts Resources : The thresholds for each of these resource types on the Outpost is shown, along with usage and availability. For example, for Amazon EC2
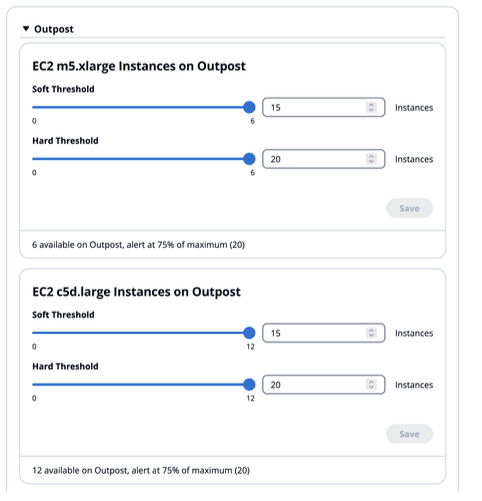
Figure 13: Outpost Resources Usage
To modify a threshold, click and drag its button. For example, to change the soft threshold to 5:
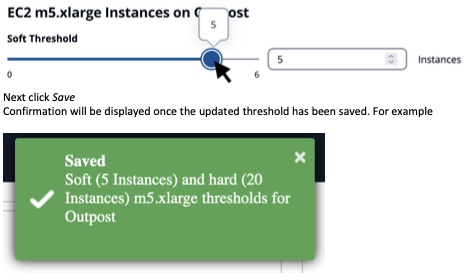
Figure 14: Modifying Resource Threshold
- Consumer Resources : The guidance supports management of Consumer resources of type
- Amazon EC2
- Amazon S3 on Outposts
Soft and hard thresholds, usage and availability are managed in the same way as for Outpost Resources, except that the thresholds work slightly differently :
- Soft Limit
- When the Consumer’s resource usage within the Outpost breaches this threshold an email is sent to the Consumer
- Hard Limit
- When the Consumer’s resource usage within the Outpost breaches this threshold the Consumer is prevented from creating new resources of this type
- When the Consumer’s resource usage within the Outpost falls below this threshold the Consumer is allowed to create new resources of this type, unless they are prevented from doing so by Outpost level thresholds
- Dashboards
Open the AWS console using the Customer account, The dashboards can be opened by clicking Dashboards within the guidance
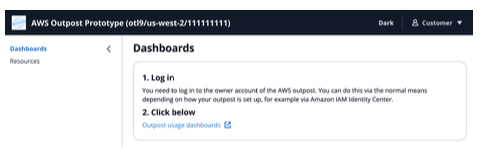
Figure 15: Guidance Dashboards
Alternatively, you can open CloudWatch within the AWS console and click on Dashboards Links to a dashboard for every Consumer, along with an aggregated dashboard for the Outpost, are shown under Custom dashboards
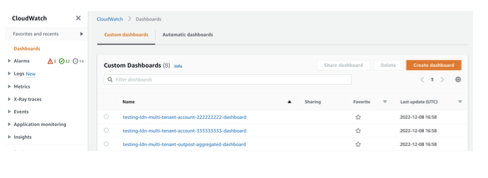
Figure 16: Amazon CloudWatch Dashboards
- Outposts Dashboard
Date Range Click Custom at the top of the dashboard to select the date range over which the dashboard should present data, such as the last four weeks
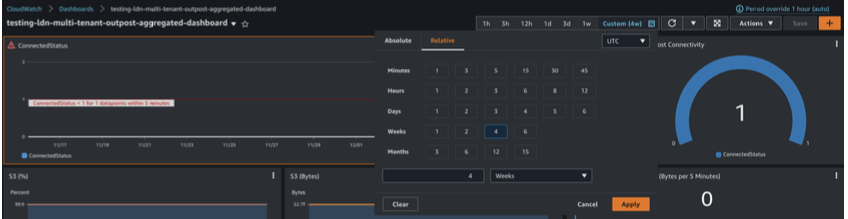
Figure 17: Data Range in the Outposts dashboards
Amazon S3 Utilization by each account, along with the remaining resource available within the Outpost is displayed. The rate of change in the total number of bytes used within the Outpost is also displayed:
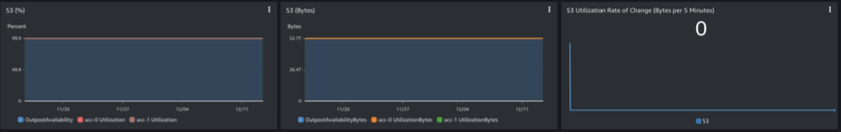
Figure 18: Amazon S3 usage
Amazon EBS Total utilization and remaining resource available within the Outpost is displayed. The rate of change in the total Gigabytes used within the Outpost is also displayed
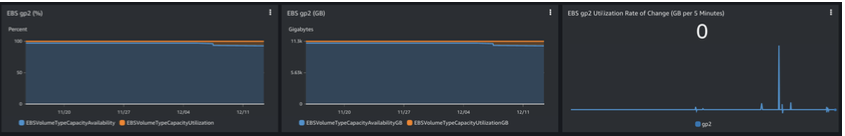
Figure 19: Amazon EBS usage
Amazon EC2 Availability and rate of change for each instance type within the Outpost are displayed Usage for each instance type by “ghost services” is also displayed. The value is calculated by subtracting the utilization by each Consumer, along with Amazon Relational Database Service (Amazon RDS), from the total utilization within the Outpost. This represents Outpost resource usage by services such as Elastic Load Balancing (ELB)
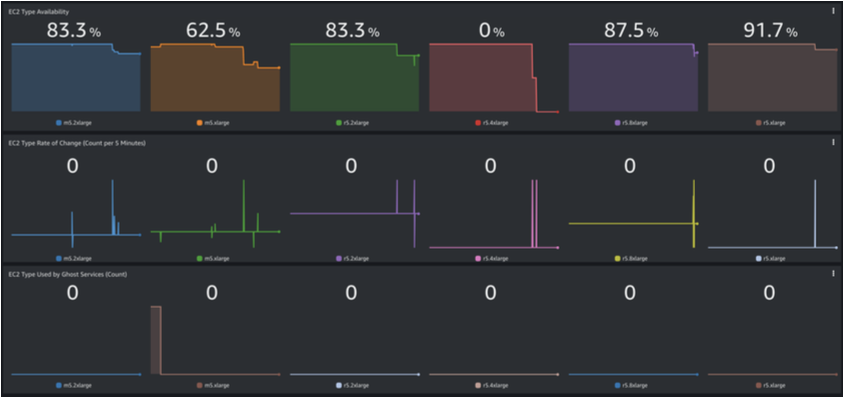
Figure 20: Amazon EC2 usage
Chargeback
The total time for which Amazon S3 and Amazon EC2 instance types have been used for is presented for each Consumer; this may potentially be used in costing calculations:
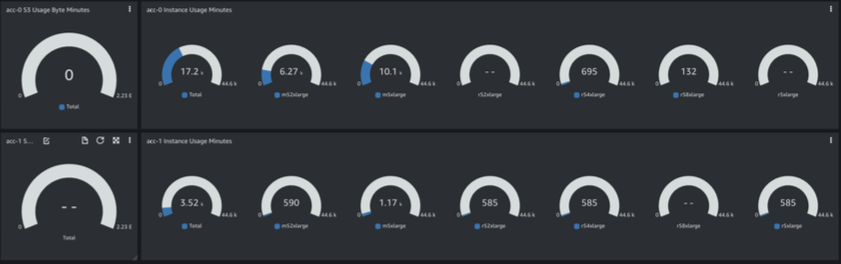
Figure 21: Chargeback data and metrics
Uninstall the Guidance
To uninstall the guidance, run the destroy command using the same stage configuration used for deployment. This will remove all infrastructure provisioned by the AWS CDK, including Lambda functions, API Gateway, IAM roles, and related resources. Before proceeding, ensure that no critical workloads or data are dependent on the deployed components. Use the following command:
pnpm cli destroy --stage <stage-name>
Replace <stage-name> with the appropriate environment (e.g., testing, dev, or prod). After successful teardown, you may optionally delete the SSO profiles from ~/.aws/config, remove any manually created IAM Identity Center applications or users, and clean up any residual data in Amazon S3 buckets if they were not automatically deleted.
Related resources
This package depends on and may incorporate or retrieve a number of third-party softwarec packages (such as open source packages) at install-time or build-time or run-time (“External Dependencies”). The External Dependencies are subject to license terms that you must accept in order to use this package. If you do not accept all of the applicable license terms, you should not use this package. We recommend that you consult your company’s open source approval policy before proceeding. Provided below is a list of External Dependencies and the applicable license identification as indicated by the documentation associated with the External Dependencies as of Amazon’s most recent review.
The license list was produced using scancode
- cc-by-4.0 AND ofl-1.1 AND mit
- This guidance relies on the following packages for its authentication, which are best to be kept up to date to keep the guidance secure.
- @nestjs/jwt
- @nestjs/passport
Contributors
- Aditya Lolla - Sr. Hybrid Edge Solutions Architect
- Daniel Zilberman - Sr. Solutions Architect, Technical Solutions
Notices
Customers are responsible for making their own independent assessment of the information in this document. This document: (a) is for informational purposes only, (b) represents AWS current product offerings and practices, which are subject to change without notice, and (c) does not create any commitments or assurances from AWS and its affiliates, suppliers or licensors. AWS products or services are provided “as is” without warranties, representations, or conditions of any kind, whether express or implied. AWS responsibilities and liabilities to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.